This challenge is looking for access control tokens in a set of provided files while mentioning source control. No one has ever committed an API key to a github repo right??
Provided Files
When you download the challenge you’re provided with a password protected zip file with the password. Opening this up, you see a pair of files, a JS file and a config.json one. Generally keys are kept in config files, so let’s see what’s in there:
{
"token": "Replace me with token when in use! Security Risk!",
"prefix": "~",
"lightNum": "1337",
"username": "UmVkIEhlcnJpbmcsIHJlYWQgdGhlIEpTIGNhcmVmdWxseQ==",
"host": "127.0.0.1"
}The username looks like base64, so if we pop that in cyberchef we see that is just a joke and returns “Red Herring, read the JS carefully”
Obviously the “token” value is the correct one, but a quick glance through the bot.js codes doesn’t make anything apparent.
Git History
Because this challenged mentioned source control, we can guess this is a git repository. In fact, ls -la confirms this:
$kali: Illumination.JS % ls -la
total 16
drwxrwxr-x@ 5 / staff 160 May 30 2019 .
drwxr-xr-x 8 / staff 256 Jan 22 23:45 ..
drwxrwxr-x@ 13 / staff 416 May 30 2019 .git
-rw-rw-r--@ 1 / staff 2635 May 30 2019 bot.js
-rw-rw-r--@ 1 / staff 199 May 30 2019 config.jsonWe have a git repo! We can actually cheese this challenge pretty easily by using tools – I already have this directory open in VS Code and it’s showing a git history on the sidebar. Heading to the config file, I can actually look at the “Timeline” which is a great feature to see changes to a file in a graphical format.
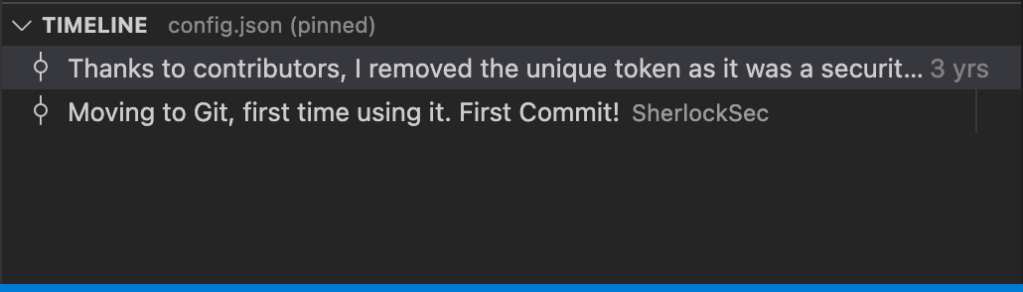
Well look at that! We go one change earlier and we see an actual token in base64 encoding (confirmed by the bot.js code). If we decode this we are left with the correct flag for the challenge. Woohoo!