Overpass is an “Easy” rated machine on THM with the goal of getting a user and a root flag. Seems pretty straightforward, only guidance is that the theme is a student-created password manager. Unfortunately we’re taking a look at this a couple years after it was created – there was a THM subscription hidden on the machine which is a pretty cool concept.
Recon
Kicking off like normal, we can start nmap to see what ports and services are available:
nmap -sV 10.10.248.94
Starting Nmap 7.93 ( https://nmap.org ) at 2023-01-22 17:26 EST
Nmap scan report for 10.10.248.94
Host is up (0.21s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Golang net/http server (Go-IPFS json-rpc or InfluxDB API)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 30.14 secondsWeb Server Recon
Since we see the web server available on port 80 we can open up a browser and check it out. I’m using the built-in browser in BurpSuite and clicking around to populate up a nice list in the HTTP history tab and to see if we want to bring anything over to Repeater or other tools.
Initially nothing really jumps out, nothing hidden in source in comments except for a note about the Romans using the type of cryptography used (ROT13 maybe?) and a “hello world” in /main.js.
The downloads page is a bit interesting, the source code for the program is listed in Go, and the download link seems to be a relative link that we can try doing a directory traversal on. Some initial quick checks don’t work (../../../etc/passwd gives a 302) so let’s move on for now.
Short of brute forcing, we can test some common paths not directly linked like /login or /admin – with some luck /admin gets us to a login screen. Taking a look at the source we see a couple JS files, login.js and cookie.js – maybe we can exploit something on the client side that should be happening on the server.
Looking at cookie.js we see a minified blob of javascript, which we can probably piece together but looks annoying at the moment, so put this aside and move to login.js.
This is a bit more useful – it looks like the username and password is sent off in a POST request, but then the response is just taken and put through some minor logic. Let’s test a dummy login to see the flow in person.
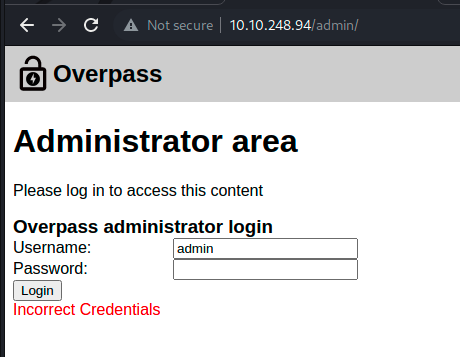
This follows what we were seeing – but maybe we can intercept that response and give something else back. We can go to the Proxy in Burp and intercept the response to a new dummy request:
We get the expected response and can modify it to literally anything else, like “Correct credentials” and forward that back. This should fix the set cookie, and after refreshing the page we get an SSH key!
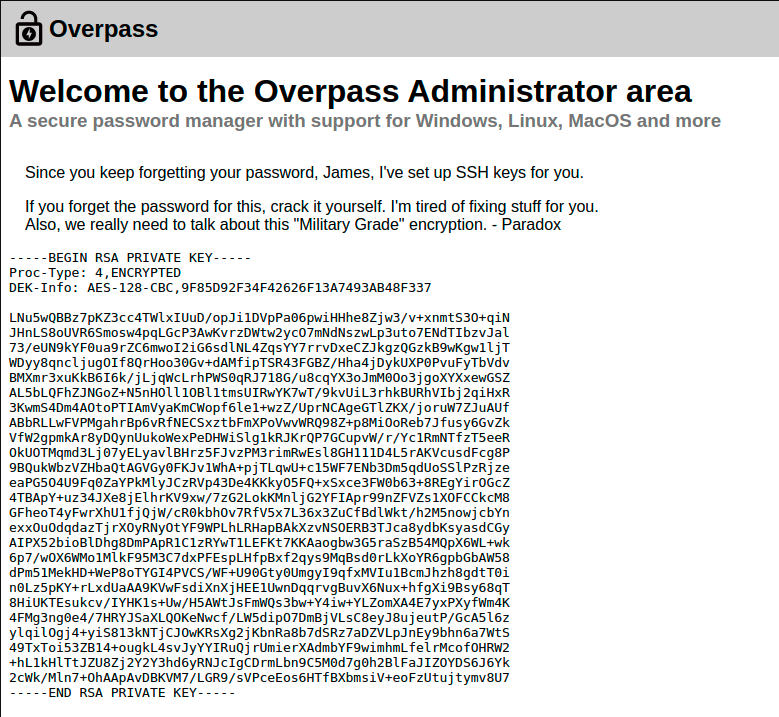
Thank you James, we can copy this and try to SSH into the server now.
Logging into the Machine
We can place the string above into something like “james_ssh.pem” and CHMOD it to 700 and attempt to login. Unfortunately this isn’t as trivial as it seems – a passcode has been set for the key (I made a typo in the key name don’t kill me):

Fortunately, tools like John the Ripper make this almost trivial to solve – we can use ssh2john to convert this into a format for john to crack:
$ ssh2john jame_ssh.pem > ssh_hash.txtRun this through john, and within seconds, we have the passkey (so much for not using things from rockyou.txt):

Now we can SSH in successfully:

A standard ls command shows us we have the user flag all set. There is a todo.txt file also in this directory, but we’ll leave it for now and see if there are other ways to get root access.
The normal sudo -l requires james’s sudo password, which we don’t have at the moment. Moving through the list of possible escalations we can check the bash history, which surprisingly shows as blank? Let’s investigate:
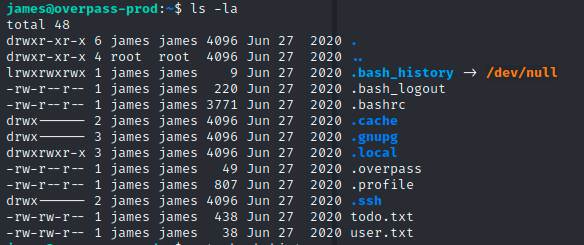
Seems the history is getting sent to /dev/null, so we can’t look there. The above output has something interesting though, .overpass seems like it could be for their password manager (this was noted in the todo list earlier). Maybe we can go there?
cat .overpass
,LQ?2>6QiQ$JDE6>Q[QA2DDQiQD2J5C2H?=J:?8A:4EFC6QNSince we’re on the machine, we can probably just use the overpass program itself to decrypt (maybe de-obfuscate is the better term…) the data above.
I was about to build it from the Go source code on the site, but on a whim found it was on the PATH.

This gets us the password for james, and unfortunately shows we can’t run sudo here, oh well:
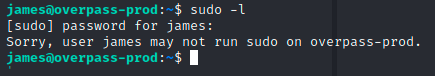
Next attempt has been my favorite on the THM boxes, checking for SUID with find / -type f -perm -04000 -ls 2>/dev/null – this also gives us no luck
Before getting too deep (capabilities also failed to find anything) I’m going to run an automated check, linPEAS, for other priv esc opportunities. Immediately we have a solid result:

A quick search of CVE-2021-4034 shows some details about it, but more importantly for the lazy like me, a metasploit module that is set up for it. Loading metasploit we first establish an SSH session (since we have a user and password):
And we’re then able to use the exploit with that session:

Popping back into our sessions list we see the new Meterpreter session and have root:


All done!